The account policies such as password and lockout policies have greatly improved in Windows Server 2008. Windows Server 2003 offered only one password and account lockout policy for all users in the domain under the Default Domain Policy. Due to which, it was not possible to set different password and account lockout settings for different sets of users.
However, Windows Server 2008 allows you to create multiple password policies for different set of users. The password policies in Windows Server 2008 are called Fine grained password and lockout policies. Although these policies appear similar to the Password Policy and Account Policy node of GPO, they are not implemented as a part of GPO. Instead, two separate object classes have been added to the AD DS for the same. These object classes are, Password Settings Container (PSC) and Password Settings.
The Password Settings Container is created by default under the System container in the domain and stores the Password Settings objects (PSOs) for that domain. You can create one or more PSO in a domain. Each PSO contain a complete set of password and lockout policy settings. A PSO can be linked to one or more security groups or users. To implement fine grained policies in your domain, the functional level of your domain must be Windows Server 2008.
The high level steps to configure the fine grained password policy include create a PSO, configuring the PSO options, assign the PSO to a user account or a global security group, and finally confirming the settings.
To configure the fine grained password policy, you need to:
- Click Start->Settings->Administrative Tools-> ADSI Edit.
- Right-click ADSI Edit and then select Connect to from the menu that appears, as shown in Figure 5-23:
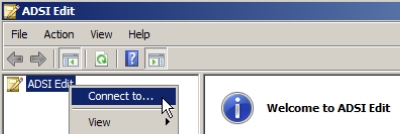
Figure 5-23 - Type Inscription.com in the Connection Settings dialog box that appears, as shown in Figure 5-24:
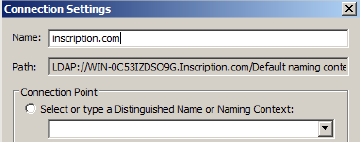
Figure 5-24 - Expand the domain and then expand DC=Inscription, DC=com.
- Expand CN=System and then
- Right-click CN=Password Settings Container and then select New->Object, as shown in Figure 5-25:
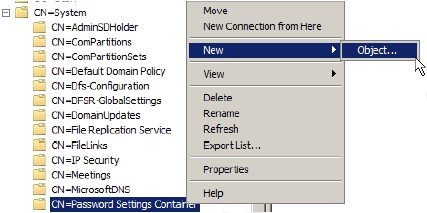
Figure 5-25 The Create Object dialog wizard appears, as shown in Figure 5-26:
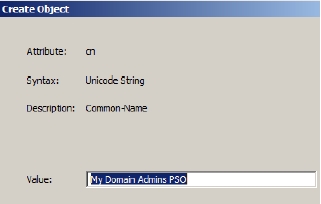
Figure 5-26 - Keep providing the settings as shown in the table and then keep clicking Next
Attribute Value Quick explanation Cn My Domain Admins PSO This is the name of the policy. msDS-PasswordSettingsPrecedence 1 This PSO has highest precedence msDSPasswordReversibleEncryptionEnabled False The password is not stored with reversible encryption. msDS-PasswordHistoryLength 32 The user cannot use any of the last 32 passwords msDS-PasswordComplexityEnabled True complex password is ensured msDS-MinimumPasswordLength 16 accounts password should be minimum 16 number of characters msDS-MinimumPasswordAge 1:00:00:00 User cannot change the password before one day msDS-MaximumPasswordAge 45:00:00:00 Must change password after every 45 days msDS-LockoutTreshold 8 The number of failed attempts before the user account will be locked msDS-LockoutObservationWindow 0:01:00:00 After 1 hr the counter for failed attempts will be reset msDS-LockoutDuration 1:00:00:00 If account will be locked it will be locked for one day - Click More attributes on the last screen of the wizard.
- In the Edit Attributes box type CN=Admins,CN=Users,DC=inscription,DC=com and click OK and then click Finish.You need to now apply the PSO to users or groups
- Open the Active Directory Users and Computers snap-in and ensure that the Advanced Features is enable in the View menu
- Go to \domain node\System\Password Settings Container and then right-click the PSO appearing in the details pane.
- Select Properties from the menu that appears.
- Click the Attribute Editor tab in the PSO Properties window that appears, as shown in Figure.
- Select the msDS-PsoAppliesTo attribute, and then click Edit, as shown in Figure 5-27.
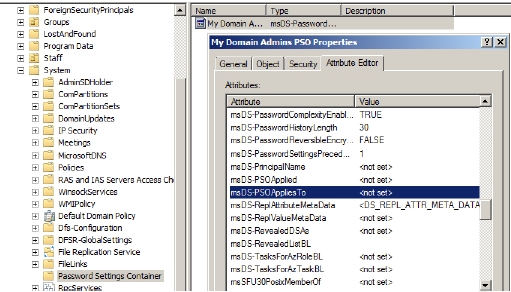
Figure 5-27 Provide the distinguished name in the Multi-valued String Editor window that appears as CN=Admins,CN=Users,DC=inscription,DC=com.
The example above have added a global security group named “Admins” with the distinguished name of “CN=Admins,CN=Users,DC=inscription,DC=com”.Every user account that is a member of this group will now be affected by this new password policy instead of the password policy defined in the Default Domain Policy.
